THM Writeup: Wonderland
Hello! Today, let’s solve TryHackMe’s challenge Wonderland. This was a pretty fun room and I learned a lot. So, let’s dive in!
Enumeration⌗
As always, I start the process with Enumeration and first thing I do while enumerating is run an nmap scan. (You might notice different IP addresses for the machine, it’s because I forgot to expand the time and my machine expired midway -_-)
Port 80 is open and the title is “Follow the white rabbit.” As the room’s theme is Alice in Wonderland, this makes sense. Let’s visit the page and see what’s happening here.
The webpage has a quote from Alice in Wonderland, and a picture of the rabbit. Next, I ran a Gobuster scan and found another directory /r.
Let’s go to the new directory and see if there’s anything useful.
Again, a quote from the book. I noticed something interesting here. The heading says “Keep Going” might it mean that there are more sub-directories here? I ran another Gobuster scan and I found another directory! This time it’s /a. Here too we find a quote and the title still says “Keep Going”. Now, just a wild guess but I thought the directories /r and /a might mean it’s trying to spell the word rabbit. So, I put /r/a/b/b/i/t and et voila!
Initial Foothold & User Shell⌗
Now, the title changes to “Open the door and enter wonderland”. This might mean something. I check the page source and sure enough, we have the credentials for the user alice!
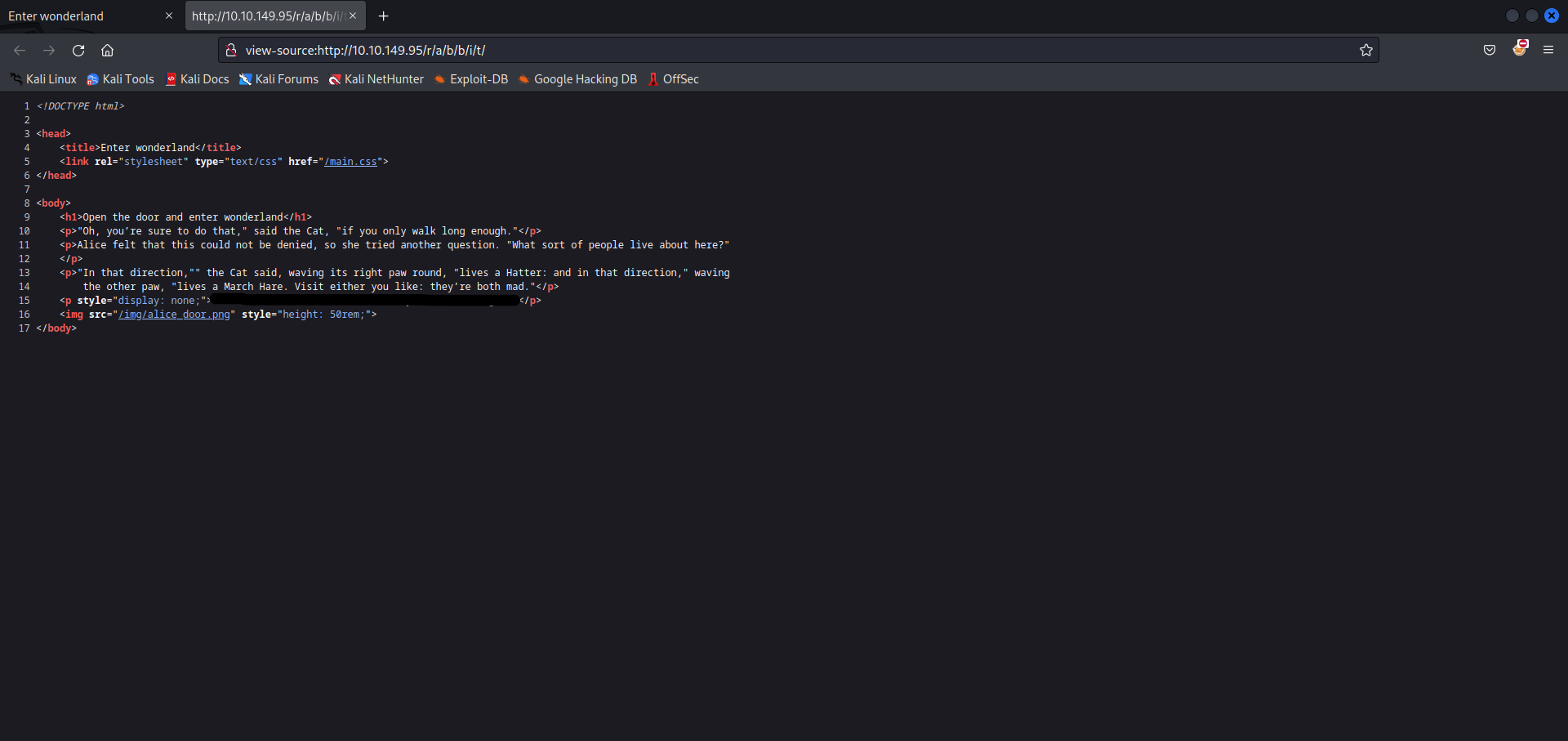
I try to SSH with these credentials and we have a shell as alice. [Hacker Voice] I’m in.
I see there’s a root.txt file in alice’s home directory instead of a user.txt file. THM’s machine page hints that “Everything is upside down here.” So, I retrieve the user.txt file from the root folder with cat /root/user.txt.
Privilege Escalation⌗
Now, I run sudo -l and see that alice can run the /usr/bin/python3.6 /home/alice /walrus_and_the_carpenter.py command as the user rabbit. We have to escalate privileges to the user rabbit somehow. We cannot edit the file walrus_and_the_carpenter.py but I can atleast look at what the code is doing.
The script is reading this poem and printing some random lines from it. What’s interesting here is that the script imports the random library. Right now, python is interpreting random as the python library. But, if we create a random.py, the code will import that and it might give us an elevated shell. This is known as python library hijacking.
Python library hijacking on Linux with examples
Let’s create a random.py file in alice’s home directory.
Now, let’s run the command as user rabbit and bingo! This gives us an elevated shell as user rabbit.
Now, rabbit’s home directory has only one file, the binary executable teaParty. I transfer this on my host machine and execute it.
So, this tells me that “Mad Hatter” will be here soon. Judging from the /etc/passwd file there is a user named hatter. I also examine the contents of teaParty and see that date variable can be hijacked. This can give us an elevated shell as hatter.
First, I will set the PATH to /tmp directory so whenever the binary file will look for the PATH it will first check the /tmp folder.
Now, we will create a date file in /tmp directory with the following contents and make it executable with chmod +x date.
This is known as path hijacking. What our binary file is doing is setting the arrival of hatter as the date. Now, with the PATH variable set, the file will look for date under /tmp directory and when it finds the shell script, it will execute the command and give us an elevated shell as hatter.
Privilege escalation Linux path hijacking
Now, let’s execute the binary.
Et voila! We have the shell as hatter. Under hatter’s home directory there is a single file called password.txt which just stores the password in cleartext. I am guessing this is hatter’s password like we had alice’s password. SSH-ing to hatter with this password gives me full shell.
Now, I run the usual linpeas.sh and find that perl executable has a capability which can help me escalated privileges.
Check out the following resources to learn more about linux capabilities.
Privilege escalation Linux Capabilities
With the help of above resource, I find a one-liner perl code to gain root privileges. I execute and bingo! The TryHackMe room Wonderland is solved!
Find the root flag under /home/alice/root.txt. I learned a lot about path hijacking and linux capabilties with this room. Thank you for reading and I will see you in the next writeup. Adios!